Linux
Scripting and Linux Customization:
I have delved into the world of Linux and Python scripting, undertaking a variety of projects aimed at automating tasks, understanding the intricacies of operating systems, and personalizing my Linux desktop environment to make it truly unique. These endeavors have not only enhanced my technical proficiency but have also provided valuable insights into how operating systems function, the power of automation, and the art of customizing Linux desktops to reflect individuality.
Project Requirements:
- Develop Linux and Python scripts to automate specific tasks and processes.
- Gain an in-depth understanding of how the Linux operating system functions.
- Customize the Linux desktop environment to create a distinctive and personalized user experience.
- Experiment with different scripting solutions to achieve efficiency and effectiveness.
What I Learned:
Through these scripting and customization projects, I’ve acquired a range of valuable skills and knowledge, including:
- Proficiency in Linux bash scripting and Python programming.
- Deeper insights into the workings of the Linux operating system.
- The ability to automate routine tasks, enhancing productivity.
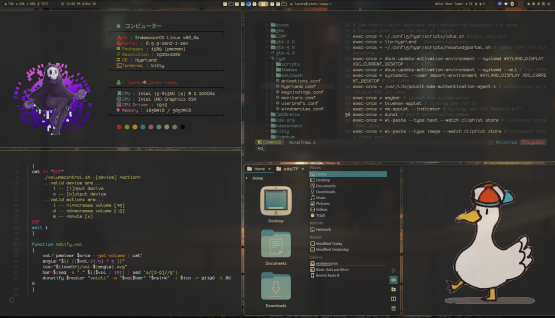
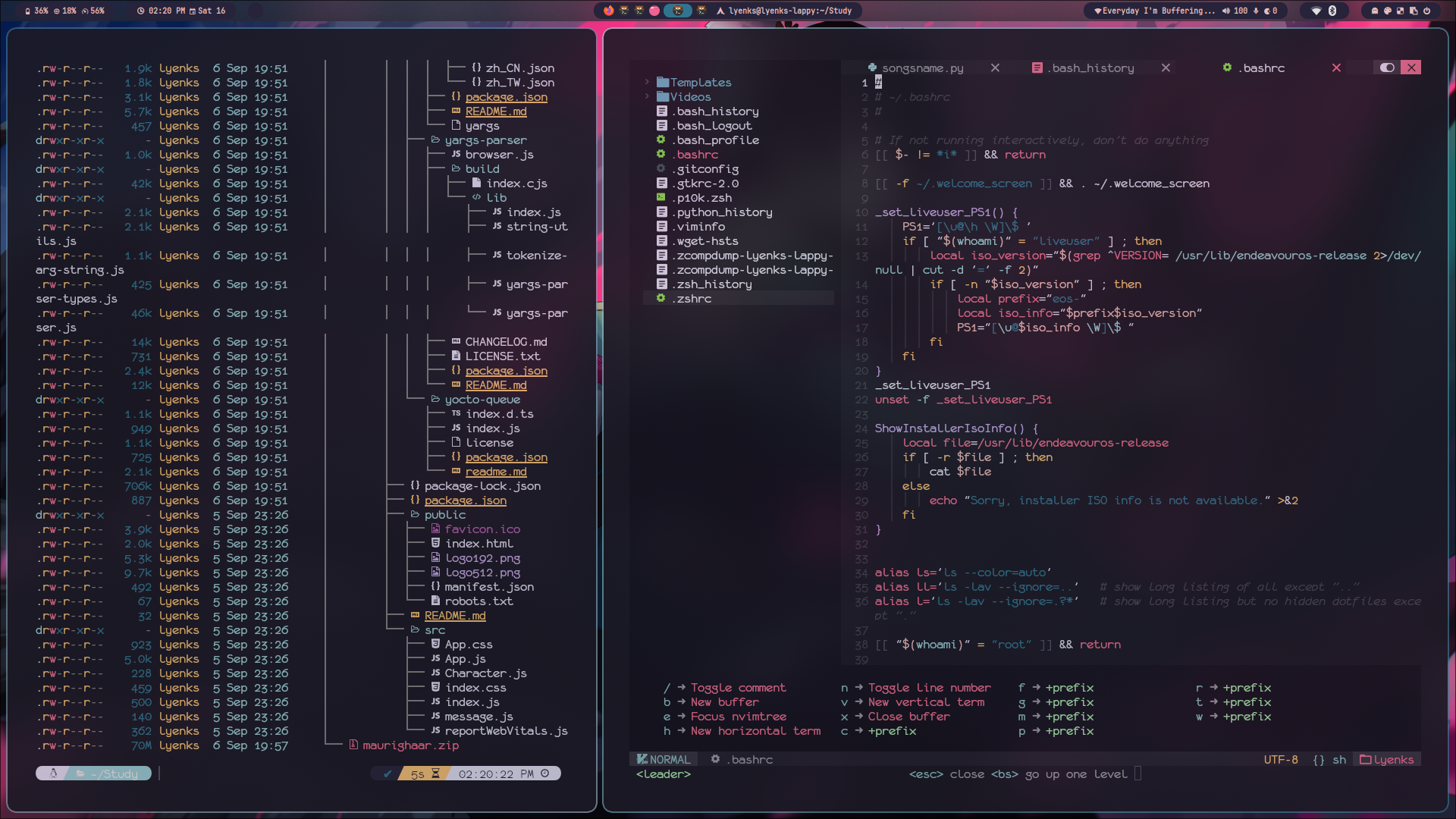
- The art of “ricing” a Linux desktop for a unique and tailored look and feel.
- Problem-solving and troubleshooting in a Linux environment.
Experiences and Personalization:
My journey into scripting and Linux customization has been an exploration of the power of open-source tools and the boundless opportunities they offer. The experiences gained through these projects have not only been technically enriching but have also allowed me to craft a Linux desktop environment that is a true reflection of my preferences and personality.
Some of my destop ricings and scripts: