Blog Posts
- Home /
- Blog Posts

My path to gain fluency in Japanese
🔠 Unearth the intricate characters that form the backbone of Japanese writing. Unlock the magic behind each stroke and immerse yourself in the rich history of this captivating script.
Read More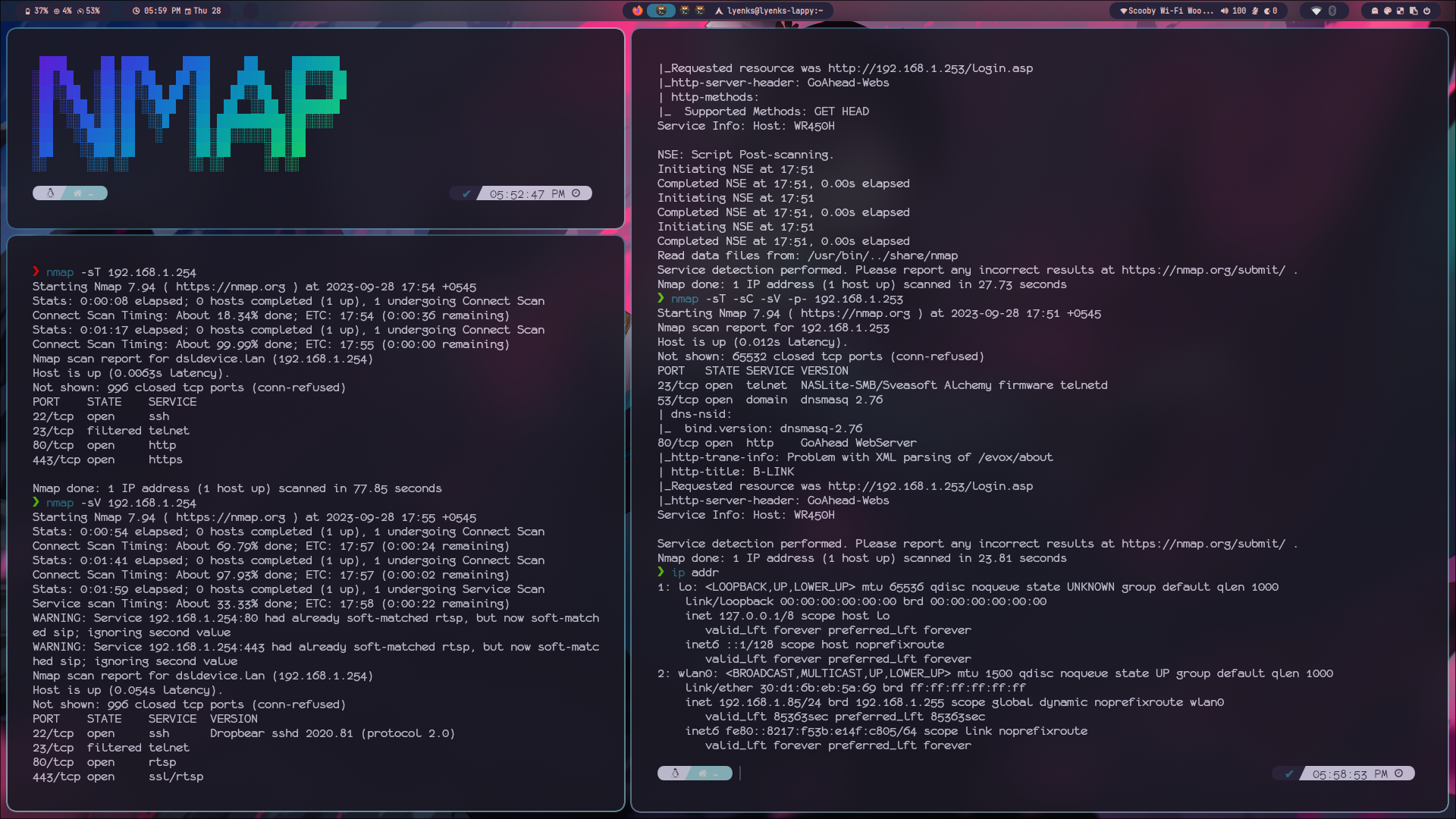
Exploring Nmap: Part 1
Every hacking starts with enumeration and reconnaissance phase. Enumeration is a crucial step in the information-gathering process and Nmap is one of the most powerful enumaration tool.
Read More
Breaking Free from Tutorial Overload
Breaking Free from Tutorial Overload: A simple guide to learning successfully and stop being on a learning treadmill but not moving forward
Read MoreCategories
Tags
- Application Centric Interface (ACI)
- Application Policy Infrastructure Controller(APIC)
- BurpSuite
- Coding
- Deployment
- Direct Server Return
- DNS
- F5 - BigIP
- F5 101
- F5-BigIP
- Git
- Github
- Half Proxy
- Hiragana
- Hosting
- Katakana
- Khanji
- Load Balancer
- Network Automation
- Network Planes
- Nmap
- OSI
- Overlay
- Penetration Testing
- Port Scanning
- Programming
- Proxy
- Python
- Software Defined Network(SDN)
- Static Sites
- TCP/IP
- Tutorial Hell
- Underlay
- Version Control System
- Virtual Extensible LAN (VXLAN)
- Vulnerability Scanning
- Web App Security
- Web Application Security
- Webapp Firewall