
TCP/IP and OSI in networking
Computer networking involves the interconnection of devices and systems for communication and resource sharing, enabling data transfer and access across various networks.
Welcome, friends, to the fascinating realm of computer networking. In this networking series, we will embark on an exciting journey to understand networking. Today we will start by exploring the intricates of the TCP/IP and OSI models, exploring each layer’s functions, protocols, and real-world examples. Prepare to dive deep into the world of networking as we unravel its mysteries together!
Understanding the Foundations: TCP/IP and OSI Models
Before delving into the complexities of computer networking, let’s lay the groundwork by introducing two fundamental models: the Transmission Control Protocol/Internet Protocol (TCP/IP) model and the Open Systems Interconnection (OSI) model. These models provide a structured framework for understanding how data is transmitted across networks.
The TCP/IP Model: Blueprint of the Internet
The TCP/IP model, often regarded as the blueprint of the internet, consists of four layers, each playing a crucial role in the communication process.
Layer 1: The Link Layer
At the bottom of the TCP/IP stack lies the Link Layer, responsible for the physical transmission of data over the network medium. This layer deals with tasks such as framing, error detection, and medium access control.
Example: Ethernet, Wi-Fi, and Bluetooth are common technologies operating at the Link Layer. Ethernet frames data into packets for transmission over twisted-pair or fiber optic cables, while Wi-Fi utilizes radio waves for wireless communication.
Layer 2: The Internet Layer
Moving up the TCP/IP stack, we encounter the Internet Layer, which focuses on routing packets across different networks. This layer enables communication between devices across the internet by assigning unique IP addresses and directing data packets to their destination.
Example: The Internet Protocol (IP) is a core protocol of the Internet Layer, responsible for addressing and routing data packets. IPv4 and IPv6 are two versions of the IP protocol used for identifying devices and facilitating communication over the internet.
Layer 3: The Transport Layer
The Transport Layer ensures reliable data delivery between hosts by providing services such as error detection, flow control, and segmentation. Protocols like TCP and UDP operate at this layer, offering different levels of reliability and connection-oriented communication.
Example: When you browse the web, TCP is responsible for ensuring that web pages load correctly by establishing a reliable connection between your device and the web server. UDP, on the other hand, is used for real-time applications such as video streaming and online gaming, where speed is prioritized over reliability.
Layer 4: The Application Layer
At the top of the TCP/IP stack lies the Application Layer, where communication between software applications takes place. This layer hosts various protocols and services that enable users to access network resources and services.
Example: HTTP (Hypertext Transfer Protocol) is a protocol operating at the Application Layer, facilitating communication between web browsers and servers. When you type a URL into your browser’s address bar, HTTP is responsible for fetching the requested web page from the server and displaying it on your screen.
The OSI Model: Architectural Masterpiece of Networking
The OSI model, developed by the International Organization for Standardization (ISO), provides a conceptual framework for understanding network communication. It comprises seven layers, each with specific functions and protocols.
Layer 1: The Physical Layer
The Physical Layer deals with the physical transmission of data bits over the network medium, including specifications for cables, connectors, and signaling.
Example: Ethernet cables, fiber optic cables, and wireless radio waves are all physical mediums used for transmitting data. Ethernet cables utilize electrical signals to transmit data over copper wires, while fiber optic cables use light signals for high-speed transmission over long distances.
Layer 2: The Data Link Layer
The Data Link Layer ensures reliable data transfer across the physical network medium by framing data into packets, detecting errors, and controlling access to the medium.
Example: Ethernet is a common protocol operating at the Data Link Layer, responsible for framing data into Ethernet frames for transmission over Ethernet networks. Ethernet frames contain destination and source MAC addresses, as well as payload data.
Layer 3: The Network Layer
Similar to the Internet Layer in the TCP/IP model, the Network Layer facilitates routing and addressing, enabling data packets to be forwarded across multiple networks.
Example: The Internet Protocol (IP) is a primary protocol of the Network Layer, responsible for routing packets across the internet. IP addresses serve as unique identifiers for devices, allowing routers to determine the best path for packet delivery.
Layer 4: The Transport Layer
The Transport Layer provides end-to-end communication between hosts, ensuring reliable and ordered delivery of data packets.
Example: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are two prominent protocols operating at the Transport Layer. TCP guarantees reliable data delivery by establishing a connection-oriented session between sender and receiver, while UDP offers connectionless communication with minimal overhead.
Layer 5: The Session Layer
The Session Layer establishes, maintains, and terminates communication sessions between applications, enabling synchronization and checkpointing.
Example: Session initiation protocols (SIP) and remote procedure call (RPC) mechanisms operate at the Session Layer, facilitating communication between applications and coordinating session management tasks.
Layer 6: The Presentation Layer
Responsible for data translation, encryption, and compression, the Presentation Layer ensures that data exchanged between applications is in a format that both sender and receiver understand.
Example: The Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols operate at the Presentation Layer, providing encryption and decryption services for secure communication over the internet.
Layer 7: The Application Layer
At the top of the OSI model resides the Application Layer, where communication between user applications and the network occurs.
Example: Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), and Simple Mail Transfer Protocol (SMTP) are common protocols operating at the Application Layer, facilitating web browsing, file transfer, and email communication, respectively.
In this extensive exploration of computer networking, we’ve journeyed through the intricate layers of the TCP/IP and OSI models, gaining a deeper understanding of how data traverses networks. Armed with this knowledge, we’re well-equipped to navigate the complexities of modern networking and embark on further adventures in the realm of computer science.
“May your connections be strong, your packets swift, and your network adventures filled with discovery!” - Networking Sage
Word Quiz
Correct := 0 | Wrong := 0
Question?
Fill the Answer
Correct:= 0 | Wrong:= 0
Question
Comments
comments powered by DisqusRelated Posts
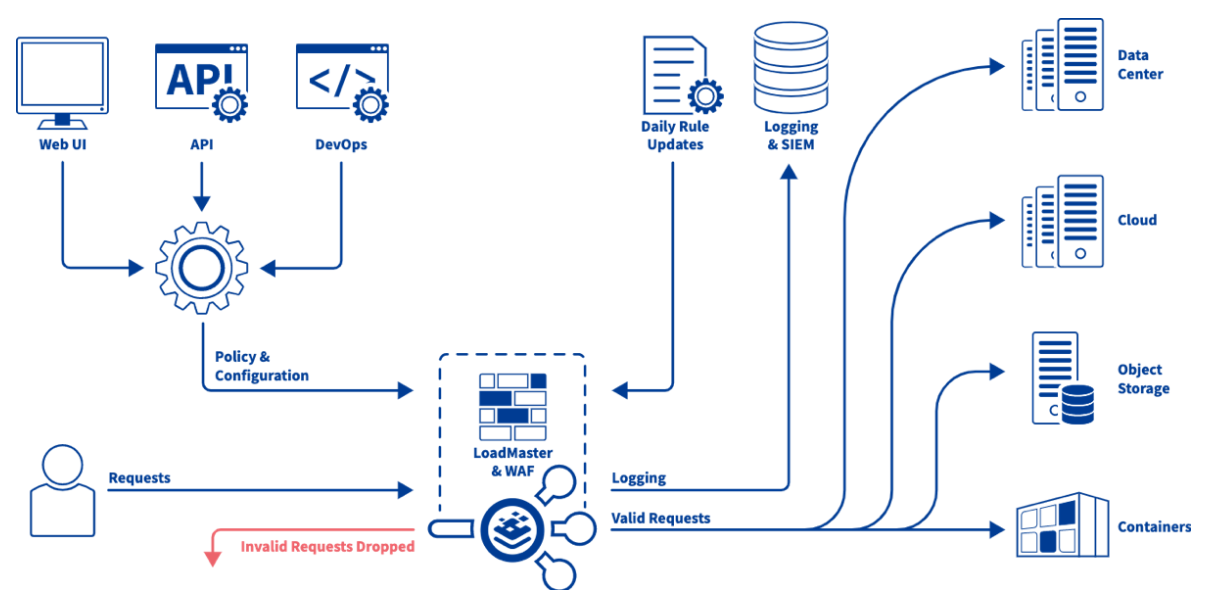
BigIP: Advanced Web Application Firewall
A comprehensive guide on advanced Web Application Firewall (WAF) policies, focusing on deployment modes, SSL/TLS integration, policy management, geolocation enforcement, and WebSocket protection to enhance security against sophisticated cyber threats.
Read More
Git Basics: Part 1
Git is a powerful version control system with a wide range of capabilities and GitHub is a popular web-based platform that provides hosting for Git repositories.
Read More
BigIP: Security Features
This comprehensive blog post provides a detailed breakdown of configuring security policies in BIG-IP ASM, covering essential elements such as policy types, enforcement modes, learning modes, and signature accuracy settings, offering practical examples and explanations for each component.
Read More