
Navigate Content
F5 101 Certification Exam
Let's Prepare for F5 101 certification exam. This is going to be the most comprehensive guide to practice for F5 101 Exam
- BIG-IP is a family of products from F5 Networks that deliver security, performance, and availability for enterprise applications.
- Components include:
- Local Traffic Manager (LTM): Helps with load balancing and traffic management.
- Application Security Manager (ASM): Protects applications against Layer 7 attacks.
- Access Policy Manager (APM): Manages and secures user access via policies.
- Global Traffic Manager (GTM): Ensures optimal user experience by managing traffic across data centers.
General Concepts
BIG-IP Full-Proxy Architecture
- Client-Side
- Server-Side
- BIG-IP operates as a full-proxy system, meaning it creates separate connections between the client and the server.
- The system encrypts and decrypts data, compresses or decompresses traffic, and translates between IPv4 and IPv6 networks.
Example flow:
- Client sends a SYN -> BIG-IP responds with SYN-ACK -> Client sends ACK -> Connection is established.
- The BIG-IP then establishes a new connection with the actual server.
- Separate client-server connections ensure that problems on the server-side do not impact client-side performance directly.
- The server-side connection is isolated, and BIG-IP controls how it interacts with the client-side.
- Load balancing techniques such as round-robin, least connections, and ratio-based balancing help distribute traffic efficiently across servers.
Example scenario:
- Client request -> Server connection established -> HTTP request processed -> Response sent back via BIG-IP to the client.
- This setup ensures consistent performance and can handle server failures without impacting the client experience.
Click here to know what a half proxy is and why it is used.
BIG-IP as Forward and Reverse Proxy
BIG-IP can act as both a forward proxy and a reverse proxy, depending on the network configuration and traffic flow needs.
Reverse Proxy
In the reverse proxy role, BIG-IP acts as an intermediary between the client and backend servers, handling requests and distributing them to the appropriate servers. This is the most common setup for load balancing, SSL offloading, and caching.
- What is a Reverse Proxy?
- Use Cases for Reverse Proxy
- A reverse proxy is a server that sits in front of web servers and forwards client (e.g. web browser) requests to those web servers.
- With a reverse proxy, when clients send requests to the origin server of a website, those requests are intercepted at the network edge by the reverse proxy server. The reverse proxy server will then send requests to and receive responses from the origin server.
Note: Reverse proxy enhances security by isolating backend servers and allowing traffic inspection and manipulation.
- Load Balancing: Distributes incoming traffic across multiple backend servers to ensure availability and reliability.
- SSL Offloading: BIG-IP decrypts incoming SSL traffic and forwards it as plaintext to the backend servers.
- Caching: BIG-IP caches frequently accessed content to improve performance and reduce backend server load.
Example: Reverse Proxy for HTTPS Traffic
tmsh create ltm virtual reverse_proxy_vs destination 0.0.0.0:443 ip-protocol tcp profiles { http http_profile clientssl client_ssl_profile } pool my_pool
This configuration:
- Listens on port 443 for HTTPS traffic.
- Uses an HTTP profile and SSL profiles to decrypt traffic.
- Distributes requests to the backend server pool (
my_pool).
Forward Proxy
As a forward proxy, BIG-IP handles outgoing traffic from internal clients to external servers, often used in corporate environments to monitor and control web access.
- What is a Forward Proxy?
- Use Cases for Forward Proxy
- A forward proxy acts on behalf of internal users, masking their IP addresses and applying policies to outgoing traffic.
- It is commonly used for content filtering, traffic control, and logging user activity.
Key takeaway: Forward proxy is often used to apply security policies on outgoing traffic, such as blocking harmful websites or controlling bandwidth.
- Content Filtering: Allows or blocks certain websites based on policies.
- Anonymous Browsing: Masks internal users’ IP addresses when accessing external sites.
- Traffic Monitoring: Tracks user activity for auditing or legal compliance.
Example: Forward Proxy for HTTPS Traffic
Example:
tmsh create ltm virtual forward_proxy_vs destination 0.0.0.0:80 ip-protocol tcp profiles { http http_profile } snat automap
This setup:
- Listens for outbound traffic on port 80 (HTTP).
- Uses source NAT (
SNAT) to hide internal client IP addresses.
Licensing and Provisioning
Activating a BIG-IP License:
- Generate a dossier from BIG-IP.
- Send the dossier to F5’s license server.
- Obtain the license from F5 and apply it to the BIG-IP system.
- Licensing can be automatic or manual.
URL for licensing: activate.f5.com
Provisioning Modules:
BIG-IP supports three provisioning levels:
- Nominal: Allocates only what’s needed, dynamically increases as needed.
- Minimum: Allocates only basic resources.
- Dedicated: All system resources are devoted to one module.
Networking in BIG-IP
Basic Networking Concepts
1. OSI Model and its Layers
The OSI (Open Systems Interconnection) model is essential for understanding networking. It defines seven layers:
| Layer | Name | Function |
|---|---|---|
| Layer 1 | Physical Layer | Hardware, transmission media, and electrical signals. |
| Layer 2 | Data Link Layer | MAC addresses, switches, and frame transmission. |
| Layer 3 | Network Layer | IP addresses, routing, and packet forwarding. |
| Layer 4 | Transport Layer | TCP/UDP, connection reliability, and flow control. |
| Layer 5 | Session Layer | Manages sessions and controls the dialogues between computers. |
| Layer 6 | Presentation Layer | Data formatting, encryption, and decryption. |
| Layer 7 | Application Layer | End-user applications and protocols like HTTP, FTP, SMTP, etc. |
BIG-IP operates at Layer 2 to Layer 7, handling routing, switching, load balancing, encryption, and web application firewall (WAF) functionalities.
2. IP Addressing and Subnetting
- IP Addressing ?
- Subnetting ?
IP addresses are crucial for identifying devices on a network. There are two main versions:
- IPv4: 32-bit address format (e.g.,
192.168.1.1) - IPv6: 128-bit address format (e.g.,
2001:0db8:85a3::8a2e:0370:7334)
IPv4 uses subnet masks to define network and host portions of an IP address, e.g., /24 or 255.255.255.0.
- Subnetting breaks a large network into smaller sub-networks or subnets. It increases efficiency and security.
For example:
- Class C network:
192.168.1.0/24 - Subnetted network:
192.168.1.0/25,192.168.1.128/25
Subnetting creates smaller subnets for traffic segmentation, making routing and traffic isolation more efficient.
Note: Subnetting is a very vast topic on itself and this is nowhere descriptive enough, so if you want to learn more about subnetting you can click here
3. VLANs (Virtual LANs)
VLANs are used to logically segment a physical network. BIG-IP uses VLANs to isolate and control traffic between different network segments.
VLAN Configuration
To create a VLAN on F5 BIG-IP, you’ll use the following command:
tmsh create net vlan internal_vlan tag 100 interfaces add { 1.1 }
In this example:
internal_vlan: Name of the VLANtag 100: 802.1Q tag (VLAN ID)1.1: Interface to associate with the VLAN
Use Case: VLANs separate user traffic from server management traffic, enhancing security by limiting broadcast domains.
Note: On a BigIP system, you can have internal and external interface on same VLAN but you cannot place management interface on same VLAN with either of internal or external VLANs.
4. ARP (Address Resolution Protocol)
ARP resolves IP addresses to MAC addresses, which are necessary for Layer 2 communication. For example, if a packet destined for 192.168.1.10 arrives, ARP will map the IP address to a corresponding MAC address using ARP requests.
# Try this command
arp -a
On BIG-IP, the ARP table stores these mappings for efficient Layer 2 traffic forwarding.
5. TCP/IP Protocol Stack
TCP/IP is the suite of communication protocols used by devices on the internet and local networks.
| Layer | Name | Protocols |
|---|---|---|
| Layer 1 | Network Access | Ethernet, Wi-Fi, ARP |
| Layer 2 | Internet | IPv4, IPv6, ICMP, IGMP |
| Layer 3 | Transport | TCP, UDP |
| Layer 4 | Application | HTTP, FTP, DNS, SMTP |
BIG-IP is primarily concerned with the Transport and Application layers, where load balancing, SSL termination, and security policies are applied.
Advanced Networking Concepts in BIG-IP
Now, let’s discuss more slightly advanced networking concepts,
1. Routing and Forwarding
Routing involves directing network traffic between different networks using routers or Layer 3 devices. BIG-IP is capable of performing routing via static or dynamic routing protocols.
- Static Routing
- Dynamic Routing (OSPF, BGP)
A static route must be configured when BIG-IP communicates with networks outside of its directly connected subnets.
tmsh create net route my_route network 192.168.2.0/24 gateway 192.168.1.1
This command creates a static route directing traffic destined for 192.168.2.0/24 through the gateway 192.168.1.1.
BIG-IP supports dynamic routing protocols such as OSPF and BGP. These protocols allow automatic route updates and adapt to network changes.
OSPF Configuration:
tmsh create net routing ospf
tmsh modify net routing ospf area 0.0.0.0
This enables OSPF on BIG-IP, where area 0.0.0.0 represents the backbone area.
2. NAT (Network Address Translation)
NAT is used to translate private IP addresses to public IP addresses (and vice versa) as packets move between private and public networks.
- SNAT (Source NAT): Changes the source IP address of outgoing traffic. Often used for outbound traffic from an internal network to external destinations.
- DNAT (Destination NAT): Changes the destination IP address of incoming traffic. Useful for directing external traffic to specific internal servers.
SNAT (Secure Network Address Translation) allows BIG-IP to hide the client’s original IP address by translating it to a local IP. This is useful for:
- Improving security by masking client identities.
- Simplifying network configurations.
- Avoiding IP conflicts.
Configuring SNAT
tmsh create ltm snat my_snat translation <internal_ip>
my_snat: The name of the SNAT configuration.<internal_ip>: The IP address to which the client’s original IP will be translated.
BigIP Application Delivery Platforms
Hardware vs. Virtual Platforms
| Platform | Advantages | Challenges |
|---|---|---|
| Hardware-based | High performance, dedicated SSL processing (e.g., VIPRION). | Expensive and less flexible, longer acquisition times. |
| Virtual-based | Fast deployment, scalable, runs on cloud environments. | Lower SSL transaction throughput compared to hardware. |
Example: BIG-IP VE (Virtual Edition) runs on Amazon AWS, while VIPRION is a high-performance hardware chassis.
F5 BIG-IP Architecture
Understanding the architecture of BIG-IP is critical for both deployment and troubleshooting. BIG-IP uses a flexible, modular architecture to provide various services such as load balancing, security, and traffic optimization.
Key Components
- TMM (Traffic Management Microkernel)
- Control Plane
- Data Plane
- TMM: The heart of BIG-IP, responsible for handling all traffic that passes through the system. TMM is highly optimized for low-latency, high-throughput traffic management and is directly integrated with the network stack.
Fun Fact: TMM bypasses the general-purpose Linux kernel to deliver higher performance.
- Control Plane: Manages administrative tasks like configuration, logging, and user authentication. It runs on the underlying Linux-based OS and handles non-traffic-related operations.
- Configuration management
- Monitoring and logging
- User authentication
- Integration with external systems
- Data Plane: The path through which traffic flows. All policies, profiles, and security measures are applied to traffic passing through this plane.
Key takeaway: The data plane is optimized to handle high-speed, low-latency traffic processing, whereas the control plane manages background tasks.
Networking Configuration in BigIP
Default BIG-IP IP Addresses
- Management IP:
192.168.1.245/24(F5 hexadecimal = 245) - Configuration commands can be performed via the TMOS shell (tmsh) or the GUI.
TMOS Operating System
BIG-IP runs on the TMOS (Traffic Management Operating System), which controls how traffic is managed through various modules.
Use the command
tmsh list sys management-ipto check management IP configurations.
- Managing BIG-IP
- Self-IP and Floating IP
- From the LCD panel, you can perform basic tasks like:
- Clearing alarms
- Reloading devices
- Managing network configuration
- Through CLI (TMOS shell):
- Example command:
tmsh save /sys ucs config_backup.ucs - This saves a backup of your system configuration to
/var/local/ucs.
- Example command:
Note: UCS backups store all critical configuration data, including SSL certificates, passwords, and licenses.
- Self-IP: IP addresses assigned to a VLAN that allow communication within a BIG-IP system.
- Floating IP: Used in failover scenarios, ensuring traffic continuity between active and standby devices.
| Type | Description |
|---|---|
| Self-IP | Internal network traffic between BIG-IP and nodes. |
| Floating IP | Shared between two or more BIG-IP systems for failover. |
Important: For high availability (HA) setups, ensure that Self-IPs are not used for external traffic.
Nodes, Pools and Pool Members
These are core elements of the BIG-IP architecture:
- Nodes: Physical or virtual servers that host the actual application.
- Pools: A collection of backend servers (nodes) that BIG-IP can distribute traffic to.
- Pool Members: A pool member is a logical object that represents a physical node (server), on the network.
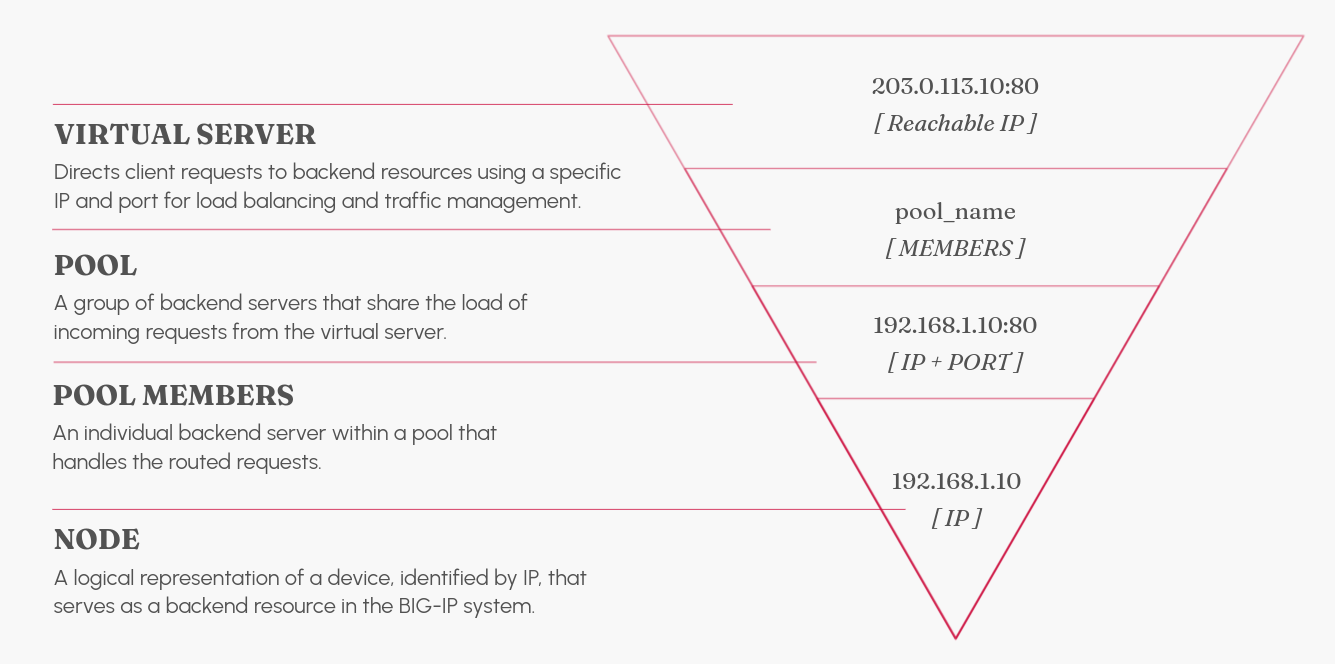
Virtual Servers
What is a Virtual Server?
A virtual server in F5 BIG-IP represents a specific IP address and port combination that BIG-IP uses to listen for incoming client requests. Virtual servers act as entry points for clients into the BIG-IP system.
Example:
Virtual Server IP: 192.168.1.100
Port: 80 (HTTP)
Types of Virtual Servers
- Standard Virtual Server
- Forwarding IP Virtual Server
- Performance (Layer 4) Virtual Server
- Standard Virtual Server: Listens for client traffic and distributes it to pool members.
- It is the most commonly used virtual server type.
Example:
tmsh create ltm virtual my_virtual_server destination 192.168.1.100:80 pool my_pool
- Associated with load balancing pools and health monitors.
- Traffic can be inspected, modified, and routed based on policies.
- Forwarding IP Virtual Server: Forwards traffic to another IP address without load balancing or modifying the traffic.
- Commonly used for simple routing scenarios or to forward traffic to another network.
Important: This type of virtual server does not perform any load balancing.
Example:
tmsh create ltm virtual my_forwarding_virtual destination 0.0.0.0:any mask 0.0.0.0 ip-forward
- Performance L4 Virtual Server: Optimized for high-speed, Layer 4 (TCP/UDP) traffic processing.
- Commonly used for DNS, streaming media, and real-time communication applications that prioritize speed over in-depth traffic inspection.
Example:
tmsh create ltm virtual my_perf_virtual destination 192.168.1.100:80 ip-protocol tcp
- Traffic is not deeply inspected, making it faster than Layer 7 virtual servers.
tmsh create ltm virtual my_vs destination 10.0.0.1:80 profiles { http } pool my_pool
This configuration:
- Creates a virtual server listening on
10.0.0.1:80. - Uses an HTTP profile to handle Layer 7 traffic.
- Sends traffic to the backend server pool
my_pool.
Traffic Management
BIG-IP provides advanced traffic management features that allow you to balance loads, prioritize certain applications, and inspect packets for security threats.
1. Load Balancing Algorithms
BIG-IP offers multiple load-balancing algorithms to distribute traffic effectively across backend servers.
Common Load Balancing Algorithms
| Algorithm | Description |
|---|---|
| Round Robin | Distributes traffic sequentially across servers. |
| Least Connections | Sends traffic to the server with the fewest active connections. |
| Fastest Response | Sends traffic to the server with the fastest response times. |
| Source IP | Routes traffic based on the client’s IP address to maintain session persistence. |
Example: Configuring Least Connections Load Balancing
tmsh modify ltm pool my_pool load-balancing-mode least-connections
In this example:
- The pool
my_pooluses the least-connections algorithm to route traffic to the server with the fewest active sessions.
Key takeaway: Choosing the right load-balancing algorithm helps optimize traffic distribution and improve application performance.
2. Persistence Profiles
Persistence profiles ensure that clients are consistently routed to the same server during their session. This is important for applications like online banking or e-commerce, where session state needs to be maintained.
Types of Persistence
- Cookie Persistence
- Source IP Persistence
- Cookie Persistence: Uses HTTP cookies to track and route clients to the same server.
tmsh create ltm persistence cookie my_cookie_persistence
This example sets up cookie-based persistence.
- Source IP Persistence: Ensures clients are routed to the same server based on their IP address.
tmsh create ltm persistence source-addr my_ip_persistence
This example sets up IP-based persistence.
3. Traffic Profiles
BIG-IP uses traffic profiles to manage specific aspects of traffic flow. Some common profiles include:
- HTTP Profile: Manages HTTP traffic, enabling features like compression, caching, and connection reuse.
- SSL Profile: Handles SSL encryption/decryption.
- TCP Profile: Manages TCP connections, optimizing throughput and latency.
Example: Configuring an HTTP Profile
tmsh create ltm profile http my_http_profile
In this example, a new HTTP profile is created to apply HTTP-specific optimizations such as request logging and compression.
Key takeaway: Profiles allow you to customize how BIG-IP handles different types of traffic, optimizing performance and security.
Health Monitors
Health monitors are critical for ensuring that traffic is only sent to healthy servers. They continuously check the availability of backend servers and mark them as available or unavailable.
Types of Health Monitors
- ICMP Monitor
- HTTP Monitor
- TCP Monitor
- ICMP Monitor: Checks the health of web servers by sending HTTP GET requests and verifying the response.
- Ideal for checking server availability.
- HTTP Monitor: Checks the health of web servers by sending HTTP GET requests and verifying the response.
tmsh create ltm monitor http my_http_monitor send "GET /health" recv "200 OK"
This example:
- Sends a GET request to the
/healthendpoint. - Marks the server as healthy if it receives a
200 OKresponse.
- TCP Monitor: Checks whether a TCP connection can be established with the server.
tmsh create ltm monitor tcp my_tcp_monitor
This example:
- Configures a basic TCP monitor to check the availability of servers by testing TCP connectivity.
Important: Health monitors ensure that traffic is not sent to unhealthy or downed servers, improving the availability of your applications.
We can also create custom health monitors according to our need.
Health monitors are used to check the status of servers and applications, ensuring that BIG-IP only sends traffic to healthy servers.
Monitor States
Monitors can result in three states for a pool member:
- Green (Up): The server is healthy, and traffic is directed to it.
- Yellow (Down): The server is not responsive or fails to meet health criteria.
- Blue (Unknown): No monitor is assigned, or the system cannot determine the server’s health.
We always configure health monitors to avoid sending traffic to unresponsive servers, which could lead to application downtime.
iApps: F5 Application Services Deployment
What is iApps?
iApps is a feature in BIG-IP designed to streamline and simplify the deployment of application services. It enables predefined templates and configurations for specific applications, providing quick, consistent, and error-free service deployment.
- Simplified Application Deployment: Pre-built templates make it easy to deploy complex services like Exchange, SharePoint, or Oracle.
- Centralized Management: All components, including virtual servers, pools, monitors, and profiles, are packaged in a single deployment.
- Customization: iApps can be tailored to fit unique network or application requirements.
- Repeatable Configurations: iApps allow you to reuse configurations, reducing human errors and ensuring consistency across deployments.
How to Create an iApp
Creating an iApp involves choosing an application template and answering a series of questions that define the configuration.
Example: Deploying a Simple HTTP iApp
- Access the iApps Menu: Navigate to iApps in the BIG-IP management interface.
- Select Application Services: Choose “Create” under Application Services.
- Choose a Template: Select a template for the application you wish to deploy (e.g., HTTP).
- Answer Configuration Questions: The template will prompt for details like virtual servers, SSL profiles, and backend server pools.
- Deploy: Once configured, deploy the iApp, which creates all the necessary objects (virtual servers, profiles, etc.).
Firewall Settings and Attack Prevention
BIG-IP includes firewall capabilities that provide deep security against various network attacks. The firewall inspects traffic based on Layer 3 (IP) and Layer 4 (Transport) headers, protecting against unauthorized access, DDoS attacks, and more.
Basic Firewall Configuration
A BIG-IP firewall configuration involves setting up rules that allow or deny traffic based on specific criteria such as IP addresses, ports, and protocols.
Example of Firewall Rule
To allow inbound traffic on port 443 (HTTPS) from a specific IP address:
Example:
tmsh create security firewall rule my_rule_1 action accept destination { address any port 443 } source { address 192.168.1.100/32 }
- Destination: Any destination server, specifically on port 443.
- Source: Only allow traffic from 192.168.1.100.
Key takeaway: Firewall rules give you control over which traffic is allowed or blocked, enhancing network security.
DDoS Protection
BIG-IP offers protection against Distributed Denial of Service (DDoS) attacks through advanced traffic management, rate limiting, and anomaly detection.
- Volume-Based DDoS: Saturates the network with massive amounts of traffic.
- Protocol-Based DDoS: Exploits protocol vulnerabilities to consume server resources (e.g., SYN flood).
- Application-Layer DDoS: Targets the application directly, such as HTTP floods or slowloris attacks.
Mitigating DDoS Attacks
BIG-IP provides a variety of methods to mitigate these attacks:
- Rate Limiting: Sets thresholds to limit the number of requests or connections from a single IP address.
- SYN Cookie Protection: Prevents SYN floods by using SYN cookies to validate incoming connections.
Example:
tmsh modify security ddos protection my_ddos_protection_profile syn-cookie enabled
- Layer 7 DDoS Protection: Mitigates application-layer attacks by filtering malicious traffic while allowing legitimate traffic to pass.
Important: DDoS protection strategies should be configured based on the specific nature of your application and the types of attacks it’s likely to face.
Logging and Monitoring
Event Logging
Event logging in BIG-IP allows administrators to capture and review important system events. This is crucial for troubleshooting and auditing.
Configuring Logging
You can enable logging for various system events, such as traffic processing, firewall rules, and security incidents.
Example:
tmsh modify sys syslog include 'authpriv.\* /var/log/auth.log'
- This command logs authentication-related events to the
auth.logfile for auditing user access.
Security Profiles
BIG-IP security profiles allow fine-grained control over how traffic is inspected and protected. These profiles include settings for SSL traffic, web application security, and protocol-specific protections.
SSL Profiles
BIG-IP uses SSL profiles to manage SSL encryption and decryption, as well as certificate handling.
Example of Creating an SSL Profile
tmsh create ltm profile client-ssl my_ssl_profile cert mycert.crt key mykey.key
This profile:
- Uses the certificate (
mycert.crt) and private key (mykey.key) to decrypt SSL traffic from the client. - Can be associated with a virtual server to handle SSL offloading.
Important: SSL profiles ensure encrypted traffic is handled properly, both in terms of security and performance.
Web Application Security (WAF)
BIG-IP can also serve as a Web Application Firewall (WAF), protecting web applications from common threats like SQL injection, cross-site scripting (XSS), and more.
Configuring a Basic WAF Policy
Example:
tmsh create security policy waf_policy defaults
This policy:
- Creates a basic WAF configuration using default settings.
- Can be further customized to detect and block specific attack vectors, such as input validation errors or unauthorized access attempts.
Key takeaway: WAF profiles add an additional layer of security to your web applications, defending against sophisticated attacks.
Attack Signatures
BIG-IP WAF includes a database of attack signatures that can be updated regularly to detect known threats. These signatures help identify and block malicious traffic.
Example of Enabling Attack Signatures
Example:
tmsh modify security waf signature-sets default enable
This command:
- Enables the default signature set to detect common attacks, such as SQL injection.
- Regular updates ensure protection against the latest threats.
Key takeaway: Attack signatures provide a proactive defense mechanism against web-based attacks, allowing for automatic blocking of known attack patterns.
iRules
iRules are TCL-based scripts that allow granular traffic control on the BIG-IP system. iRules are often used to:
- Inspect Traffic: Analyze incoming HTTP requests for signs of malicious activity.
- Modify Traffic: Redirect or rewrite requests based on specific criteria.
- Log and Monitor: Log suspicious requests for auditing purposes.
Example: Simple iRule for Redirection
when HTTP_REQUEST {
if { [HTTP::uri] starts_with "/old" } {
HTTP::redirect "http://example.com/new"
}
}
This iRule:
- Checks if the requested URI starts with
/old. - Redirects the client to
http://example.com/new.
Example: Basic Security iRule to Block SQL Injections
when HTTP_REQUEST {
if { [HTTP::uri] contains "select" } {
reject
}
}
This iRule blocks any requests that contain the keyword “select” in the URI, which is a basic check for SQL injection attempts.
Advanced iRule for XSS Protection
when HTTP_REQUEST {
if { [HTTP::uri] contains "<script>" } {
reject
}
}
This iRule rejects requests containing <script> tags, providing basic protection against Cross-Site Scripting (XSS) attacks.
To learn more about iRules you can click here
Key takeaway: iRules offer flexibility in handling traffic by allowing custom logic for traffic inspection, modification, and routing.
Troubleshooting BIG-IP Systems
Troubleshooting is a critical skill for managing F5 systems. You’ll need to understand how to identify and resolve network, application, and configuration issues.
Common Troubleshooting Steps
1. Check Network Connectivity
Before diving into more complex issues, ensure that basic network connectivity is functioning correctly.
ping <destination IP>
Use the ping command to verify that the BIG-IP system can reach upstream or downstream devices.
2. Monitor Traffic Using tcpdump
BIG-IP allows packet-level analysis using tcpdump, a powerful command for capturing traffic.
tcpdump -i 0.0:nnn -w /var/tmp/capture.pcap
-i 0.0:nnn: Captures traffic on all TMM interfaces.-w /var/tmp/capture.pcap: Writes the packet capture to a file.
Once captured, you can analyze the traffic in detail using tools like Wireshark.
Pro Tip: Always capture traffic on the TMM interface (
0.0) for more comprehensive results, as it’s responsible for most traffic processing.
3. Check Logs
BIG-IP maintains several logs that can help diagnose problems.
| Log File | Description |
|---|---|
/var/log/ltm | Logs related to Local Traffic Manager (virtual servers, pools, etc.). |
/var/log/tmm | Logs related to TMM engine errors. |
/var/log/secure | Logs related to system security events. |
To view logs:
tail -f /var/log/ltm
This command displays real-time logs for LTM, useful for monitoring issues as they occur.
4. Diagnose iRules
When iRules are involved, you can troubleshoot by using logging statements inside the iRule. For example:
when HTTP_REQUEST {
log local0. "Request received for [HTTP::uri]"
}
This logs the requested URI, helping you trace any issues related to traffic routing or manipulation.
5. Verify Node Health
If traffic isn’t reaching a pool member, verify that the node is marked as “available.”
tmsh show ltm pool <pool_name> members
Check if the pool members are marked as up or down. If a member is down, investigate health monitors or connectivity issues.
High Availability (HA)
Overview of BIG-IP High Availability
High availability (HA) ensures that services remain accessible even if a device fails. BIG-IP systems can be configured in active/standby or active/active modes.
- Active/Standby: One unit is actively processing traffic, and the other remains on standby, ready to take over if the active unit fails.
- Active/Active: Both units process traffic, but they monitor each other for failover.
HA Architecture
1. Failover Mechanism
Failover occurs when the active device fails or becomes unavailable. In HA, failover is triggered by:
- Loss of heartbeat messages between devices.
- Resource exhaustion (e.g., CPU or memory overload).
- Link failure (network card or switch outage).
2. Configuring HA
Setting up HA involves defining device groups, traffic groups, and synchronization methods.
Device Group: A collection of devices that participate in HA. These devices share configurations and monitor each other for failover events.
Traffic Group: Contains all the virtual servers and configurations that will failover from one device to another.
ConfigSync: Synchronizes configuration changes across devices to ensure they have identical settings.
Key takeaway: Ensure that device groups are configured correctly, and always perform a config sync after making any changes.
Steps to Configure HA
1. Create a Device Group
tmsh create cm device-group HA_Group type sync-failover devices add { <device_1> <device_2> }
type sync-failover: Specifies that this group will be used for failover and configuration synchronization.devices add { <device_1> <device_2> }: Adds the devices that will participate in the HA group.
2. Assign Traffic Groups
tmsh create cm traffic-group traffic-group-1
traffic-group-1: Specifies that this traffic group will contain the virtual servers and configurations that will failover.
3. Enable ConfigSync
To manually sync configurations across devices:
tmsh run cm config-sync to-group HA_Group
This ensures that both devices are using the same configurations.
Optimizing System Performance
For large-scale deployments, performance optimization is crucial to ensure BIG-IP can handle traffic without performance bottlenecks.
Traffic Profiles and Optimization
Using optimized profiles can significantly improve performance.
1. TCP Profile Optimization
A well-tuned TCP profile improves the throughput and response times of your applications.
tmsh modify ltm profile tcp my_tcp_profile idle-timeout 300 recv-window-size 65536
idle-timeout 300: Sets the idle timeout to 300 seconds, reducing resource consumption for inactive connections.recv-window-size 65536: Increases the receive window size to optimize data throughput.
Best Practice: Customize TCP profiles for specific application needs instead of using the default.
2. SSL Profile Optimization
SSL offloading is resource-intensive, so optimizing SSL profiles can reduce CPU usage and latency.
tmsh modify ltm profile client-ssl my_ssl_profile ciphers 'ECDHE+AESGCM'
ECDHE+AESGCM: Optimizes SSL performance by using modern, secure, and efficient ciphers.
Pro Tip: Keep SSL certificates and keys optimized by using the latest encryption standards like TLS 1.3.
3. Connection Reuse
Enable HTTP connection reuse to reduce the number of TCP handshakes required for new connections.
tmsh modify ltm profile http my_http_profile connection-reuse enabled
This reduces latency for HTTP traffic by reusing existing connections for subsequent requests.
BIG-IP Advanced Firewall Manager (AFM)
AFM helps secure the network from DoS attacks, volumetric threats, and other forms of intrusion at different layers of the OSI model.
Key Features of AFM
- Layer 3-4 DoS Protection: Protects against common Layer 3 and Layer 4 attacks, like SYN floods and UDP-based attacks.
- IP Intelligence: Provides real-time threat intelligence by monitoring IP addresses to block or allow traffic based on threat levels.
- Network Firewall Policies: Configure ACLs (Access Control Lists) that control traffic based on source/destination IPs, ports, and protocols.
Basic AFM Configuration Example
tmsh create security firewall policy my_firewall_policy
tmsh create security firewall rule my_firewall_rule source { any } destination { any } action accept
This creates a firewall policy allowing traffic from any source to any destination.
Best Practice: Use ACLs to restrict traffic to only trusted sources and services.
SSL Offloading on BIG-IP
SSL Offloading is the process of decrypting SSL traffic at the BIG-IP device so that backend servers do not need to handle the decryption. This reduces the load on servers and allows BIG-IP to inspect traffic more efficiently.
SSL offloading terminates the SSL connection at the F5 device, and forwards the request to the backend server in plain HTTP. This frees the server from the CPU-intensive SSL processing.
Advantages:
- Reduced server load.
- Centralized SSL certificate management.
- Ability to inspect and manipulate encrypted traffic for security purposes.
2. Types of SSL Offloading
There are two types of SSL processing in BIG-IP:
- SSL Termination: SSL is terminated at BIG-IP, and plain HTTP traffic is sent to the backend servers.
- SSL Bridging: BIG-IP decrypts the traffic, inspects or modifies it, and then re-encrypts it before forwarding it to the backend server.
SSL Termination Example
tmsh create ltm virtual my_https_vs destination 192.168.1.100:443 profiles add { clientssl }
This creates a virtual server to handle SSL traffic using a clientssl profile.
3. Creating SSL Profiles
SSL profiles define how SSL connections are managed. There are client SSL profiles for inbound SSL traffic and server SSL profiles for outbound SSL traffic.
Example: Creating Client SSL Profile
tmsh create ltm profile client-ssl my_ssl_profile
This command creates a basic client-side SSL profile. You can attach this profile to a virtual server that handles incoming HTTPS traffic.
Example: Creating Server SSL Profile
tmsh create ltm profile server-ssl my_server_ssl_profile
A server SSL profile is used when the traffic between BIG-IP and the backend server needs to remain encrypted (SSL Bridging).
4. Installing SSL Certificates
To enable SSL offloading, an SSL certificate needs to be installed on the BIG-IP device.
Steps for Installing an SSL Certificate
- Upload the certificate: You can upload certificates via the web GUI or use
tmshcommands.
tmsh install sys crypto cert my_cert.crt
- Create SSL Profile: Associate the certificate with the SSL profile.
tmsh create ltm profile client-ssl my_ssl_profile cert my_cert.crt key my_key.key
This configuration enables SSL offloading for both client-side and server-side traffic.
5. Attaching SSL Profiles to a Virtual Server
Once the profiles are created, they must be attached to the virtual server.
tmsh modify ltm virtual my_virtual_server profiles add { my_client_ssl_profile my_server_ssl_profile }
This associates the SSL certificate and key with the SSL profile used for client-side SSL offloading.
Compression
Compression reduces the size of HTTP responses, improving page load times and reducing bandwidth usage. BIG-IP supports HTTP and GZIP compression, making it useful for text-based content like HTML, CSS, and JavaScript files.
Benefits of Compression
- Improved Page Load Times: Compressed content is smaller, so it loads faster for users.
- Reduced Bandwidth Costs: Compressed traffic uses less bandwidth, which is especially useful in environments where bandwidth costs are high.
Configuring HTTP Compression
tmsh create ltm profile http-compression my_compression_profile gzip enable
In this example, GZIP compression is enabled for the profile. You can fine-tune the profile by adjusting compression settings for different content types.
Attaching Compression Profile to a Virtual Server
Once the compression profile is configured, it needs to be attached to a virtual server.
tmsh modify ltm virtual my_virtual_server profiles add { my_compression_profile }
This will ensure that HTTP traffic is compressed before being sent to the client.
Web Application Firewall (WAF) - ASM
The Application Security Manager (ASM) is F5’s Web Application Firewall (WAF) designed to protect web applications from attacks such as:
- Cross-Site Scripting (XSS)
- SQL Injection
- Remote File Inclusion (RFI)
- Command Injection
ASM inspects incoming traffic to detect and block malicious requests while allowing legitimate traffic through.
Key Features of ASM
- Positive Security Model: Only allows requests that match the predefined rules. Anything outside of this is considered suspicious and blocked.
- Threat Intelligence: Provides real-time threat updates to protect against newly discovered vulnerabilities and attack vectors.
- Attack Signatures: ASM uses a database of attack signatures to detect and block known attacks automatically.
Basic WAF Policy Configuration
A WAF policy can be configured to protect specific applications. Here’s a quick example:
tmsh create asm policy my_waf_policy
tmsh modify asm policy my_waf_policy status active
tmsh modify asm policy my_waf_policy signatures { "SQL Injection" "XSS" }
This creates and activates a WAF policy that blocks SQL injection and XSS attacks.
Attach WAF Policy to a Virtual Server
Once the WAF policy is configured, it needs to be applied to a virtual server.
tmsh modify ltm virtual my_virtual_server policies add { my_waf_policy }
This ensures that traffic passing through the virtual server is inspected and filtered by the WAF.
Common Use Cases for ASM
- Protecting Web Applications: By monitoring and filtering HTTP traffic, ASM helps protect web applications from various vulnerabilities.
- Compliance Requirements: Many organizations need WAFs to meet security standards like PCI-DSS, which mandates the protection of web applications.
Security Best Practices
- Regularly Update ASM Signatures: Always keep your ASM attack signatures up to date to stay protected against the latest vulnerabilities.
- Use SSL Everywhere: Ensure that all traffic (client-side and server-side) is encrypted with the latest TLS protocols to protect against data breaches.
- Tune WAF Policies: Regularly review and tune your WAF policies to balance security with performance and avoid false positives.
- Enable Logging: Ensure that critical security events are logged and monitored in real-time. Use logging tools and centralized monitoring to detect unusual patterns.
Persistence in BIG-IP
Persistence ensures that a client’s subsequent requests are directed to the same server in a load-balanced pool, which is crucial for session-based applications.
1. Why is Persistence Important?
Persistence (also called stickiness) is necessary when:
- Users have session data stored on a particular server.
- Long-running transactions or connections require consistent routing to the same backend server.
2. Types of Persistence Methods
F5 BIG-IP supports various persistence methods:
| Persistence Method | Description |
|---|---|
| Source Address | Uses the client’s source IP address to maintain session stickiness. |
| Cookie Persistence | Inserts a cookie in the client’s browser to ensure it returns to the same server. |
| SSL Persistence | Ties the persistence to an SSL session ID. |
| Hash Persistence | Uses a hash (e.g., URI or IP) to distribute traffic. |
| Destination Address | Based on the destination address (for servers that balance clients based on destination). |
Example: Configuring Cookie Persistence
tmsh create ltm persistence cookie my_cookie_persistence method insert
tmsh modify ltm virtual my_vs profiles add { my_cookie_persistence }
This example inserts a cookie into the client’s browser to achieve persistence.
3. Persistence Timeout and Granularity
Persistence profiles can be configured with timeouts to specify how long persistence is maintained.
tmsh modify ltm persistence cookie my_cookie_persistence timeout 3600
This sets the persistence timeout to 3600 seconds (1 hour).
Application Acceleration with BIG-IP
BIG-IP offers a range of features to accelerate application delivery, reduce latency, and optimize bandwidth usage.
1. Compression
BIG-IP can compress HTTP responses before sending them to clients. This reduces bandwidth usage and speeds up web page load times.
Example: Enabling Compression
tmsh create ltm profile http-compression my_compression_profile
tmsh modify ltm virtual my_vs profiles add { my_compression_profile }
The http-compression profile ensures that content is compressed before being sent to the client.
2. Caching
F5 BIG-IP can cache HTTP responses and serve them directly to clients, reducing the need to contact the backend server for every request.
Example: Enabling Web Acceleration (Caching)
tmsh create ltm profile web-acceleration my_cache_profile
tmsh modify ltm virtual my_vs profiles add { my_cache_profile }
This enables caching for a virtual server, reducing load on backend servers.
Security Features in BIG-IP
Now, let’s dive into the security features of BIG-IP. This includes Advanced Firewall Manager (AFM) and Application Security Manager (ASM), which provide firewall protection and application layer security, respectively.
1. Advanced Firewall Manager (AFM)
AFM is a network firewall that protects applications and networks by providing stateful packet inspection and deep threat analysis.
Key Features:
- DoS Protection: AFM mitigates Denial of Service (DoS) attacks by detecting and blocking malicious traffic.
- Traffic Filtering: Uses Layer 3/4 rules to filter traffic based on source IP, destination IP, ports, etc.
- Rate Limiting: Throttles excessive traffic from malicious actors.
Example: Creating an AFM Rule to Block IP Traffic
tmsh create security firewall rule-list block_ip_list rules add { block_ip_rule { action drop destination { addresses add { 10.10.10.10 } } } }
This rule drops traffic destined for 10.10.10.10.
Section 4: Security
4.01 – Compare and Contrast Positive and Negative Security Models
- Positive Security Model (Whitelist)
- Negative Security Model (Blacklist)
A positive security model only allows traffic or actions that are explicitly permitted and blocks everything else by default.
Example: A firewall rule that only allows HTTP (port 80) traffic and blocks all other ports.
Advantages:
- More secure by design as only known-good traffic is allowed.
- Can block new, unknown attacks (Zero-day).
Disadvantages:
- Difficult to configure initially due to needing to define all valid traffic patterns.
- Risk of legitimate traffic being blocked if not included in the whitelist.
A negative security model allows all traffic except for explicitly denied actions.
Example: An Intrusion Prevention System (IPS) that blocks known malicious traffic patterns or signatures.
Advantages:
- Easier to implement initially as only malicious traffic needs to be blocked.
- Allows more flexibility for new, unknown traffic.
Disadvantages:
- Can miss Zero-day attacks because only known malicious behavior is blocked.
Takeaway: Positive security models (whitelisting) are more secure but harder to configure, while negative security models (blacklisting) are easier to implement but less secure.
Cryptographic Services
Cryptographic services are essential for securing data in transit and ensuring the authenticity and integrity of communication.
Signing: A method to verify the integrity and authenticity of a message or document.
- Uses asymmetric encryption where a private key signs the data, and the public key verifies it.
Encryption: The process of converting plaintext into ciphertext to protect data.
- Symmetric Encryption: The same key is used to encrypt and decrypt data (e.g., AES).
- Asymmetric Encryption: Different keys are used for encryption (public) and decryption (private) (e.g., RSA).
Certificates: Digital certificates bind a public key to an entity (like a domain). They are signed by a trusted Certificate Authority (CA).
- Certificate Chain: A chain of trust from a root CA to an intermediate CA and the end-user certificate.
- If an issuing CA is revoked, all certificates it issued are no longer trusted.
Example: SSL certificates used for HTTPS websites provide encryption and authenticity.
Authentication Methods
Authentication is the process of verifying that a user or device is who they claim to be.
Types of Authentication:
| Method | Description |
|---|---|
| Password | Something the user knows (passwords or passphrases). |
| Token-based | Something the user has (RSA token, Google Authenticator). |
| Biometric | Something the user is (fingerprint, facial recognition). |
Single Sign-On (SSO)
SSO allows users to authenticate once and access multiple applications without having to log in again.
Multi-Factor Authentication (MFA)
MFA requires two or more authentication factors to verify a user’s identity (e.g., password + SMS code).
4.04 – IPsec and SSL VPN
- IPsec VPN
- SSL VPN
IPsec is a suite of protocols for securing IP communications by authenticating and encrypting each IP packet.
Advantages:
- Provides security for site-to-site VPNs (e.g., connecting two branch offices).
Disadvantages:
- More complex to set up for remote users compared to SSL VPN.
SSL VPN provides secure access to corporate networks over a browser using SSL/TLS encryption.
Advantages:
- Easier to deploy than IPsec for remote users.
- Typically operates over TCP 443, bypassing firewalls.
Example: Using SSL VPN for remote access to corporate applications.
Advanced Acceleration Techniques
Acceleration techniques improve the speed and performance of application delivery.
- TCP Optimization
- HTTP Caching
- Compression
- Selective Acknowledgments: TCP feature that helps recover from packet loss more efficiently.
- Connection Pooling: Reuses existing TCP connections to reduce the overhead of creating new ones.
Example: BIG-IP can pool server-side TCP connections to reduce load on servers.
- Web Caching: Stores HTTP responses and serves them to clients without contacting the backend server for every request.
Example: A content delivery network (CDN) caches images and static content closer to users.
- GZIP Compression: Reduces the size of HTTP responses, speeding up page load times and saving bandwidth.
Example: Compressing large HTML, CSS, and JavaScript files using GZIP on BIG-IP.
Additional Resources
Word Quiz
Correct := 0 | Wrong := 0
Question?
Fill the Answer
Correct:= 0 | Wrong:= 0
Question