Exploring Nmap: Part 1
Every hacking starts with enumeration and reconnaissance phase. Enumeration is a crucial step in the information-gathering process and Nmap is one of the most powerful enumaration tool.
Nmap (Network Mapper) is a powerful and widely-used open-source network scanning and security auditing tool designed to discover devices, services, open ports, and potential vulnerabilities on computer networks.
Every hacking starts with enumeration and reconnaissance phase. Enumeration is a crucial step in the information-gathering process when assessing the security of a network or system. During this phase, the goal is to gather as much information as possible about the target network or system to identify potential vulnerabilities and weaknesses.
Installing Nmap
Windows
Windows users can download the official Nmap installer from the Nmap’s website and follow the installation wizard. Make sure to add Nmap to your system’s PATH for convenient command-line access.
Nmap can also be installed in windows using winget. Open powershell and type the following the following command:
winget install -e --id Insecure.Nmap
Linux
On Linux, the installation process is as straightforward as it can get. Just open the terminal and use the package manager according to the distribution:
For Debian/Ubuntu:
sudo apt install nmap
For Red Hat/CentOS/Fedora:
sudo dnf install nmap
For Arch:
sudo pacman -S nmap
macOS
macOS users can use the Homebrew package manager for a hassle-free installation:
brew install nmap
Alternatives for Android and iOS
While Nmap is primarily designed for desktop and server environments, if an android or iOS is all that you’ve got don’t worry I got you. Here are some alternatives you can use:
Android:
- Fing Network Tools: Fing is a nice and user-friendly app that can help you discover devices on your network, check their connectivity, and perform basic network enumeration.
- Termux: Advanced users can install Termux, a terminal emulator for Android, and then install Nmap within it to use Nmap. Termux is basically linux at your fingertips. In termux to download nmap you can use the command:
pkg install nmap
iOS:
- iNetTools: iNetTools offers a set of network diagnostic tools, including ping, traceroute, and port scanning, for iOS users.
- Termius: Similar to Termux on Android, you can use the Termius app on iOS to run Nmap commands within a terminal environment. This is what google search said as I haven’t used iOS yet.
Let’s start using Nmap
Nmap requires some stuff before starting to scan a network. Those things include:
- IP address and subnet
- Port number
- Scan Type
- Timings
- Output Type
Host Discovery
First and foremost Nmap utilizes host discovery to make sure the host is alive and running. Scans require a lot of time to be performed. When there are a lot of IPs to be scanned it makes more sense to not scan the devices that are not active to save time. -Sn flag is used for host discovery and it can be disabled using the -Pn flag. Nmap performs host discovery by default even when -Sn is not explicitly mentioned.
nmap -Sn 192.168.10.2
nmap -Pn 192.168.10.2
We skip the host discovery phase if we know that our target is up. This command will make the Nmap scan the network without host discovery.
When we perform scan as root
- Nmap sends an ICMP echo packet
- Nmap sends a TCP SYN packet on port 443
- Nmap sends a TCP ACK packet on port 80
- Nmap sends ICMP timestamp request
When we perform scan as local user
- Nmap sends a TCP SYN packet on port 443
- Nmap sends a TCP ACK packet on port 80
If Nmap receives response from any of these, it will confirm that the host is active and begins port scanning.
Nmap utilizes the TCP handshake to check if the port is active or not.
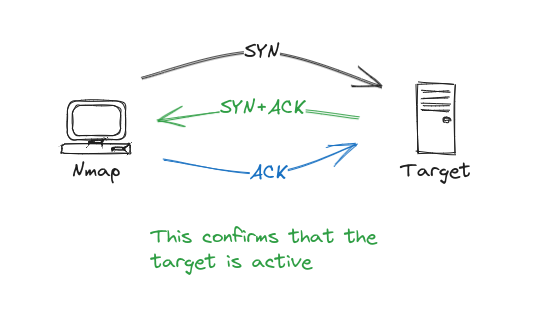
- If the target is active then it replies to Nmap’s SYN packet with a SYN+ACK packet which will tell the Nmap that the target is up.
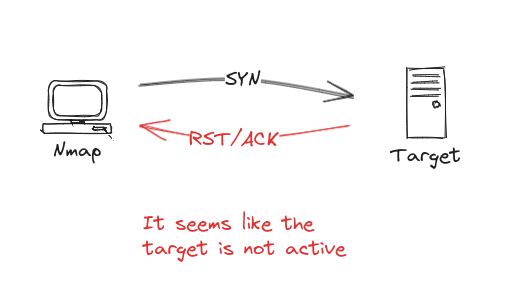
- If the target is down then it replies to Nmap’s SYN packet with a RST/ACK packet which will tell the Nmap that the target is down.
Word Quiz
Correct := 0 | Wrong := 0
Question?
Fill the Answer
Correct:= 0 | Wrong:= 0
Question
Comments
comments powered by DisqusRelated Posts

BigIP: Security Features
This comprehensive blog post provides a detailed breakdown of configuring security policies in BIG-IP ASM, covering essential elements such as policy types, enforcement modes, learning modes, and signature accuracy settings, offering practical examples and explanations for each component.
Read More
Software Defined Networking
This is going to sound weird but your current knowledge of networking is going to be worthless after SDN takeover. Wanna know why?
Read More
Breaking Free from Tutorial Overload
Breaking Free from Tutorial Overload: A simple guide to learning successfully and stop being on a learning treadmill but not moving forward
Read More